CVE-2023-41179
Trend Micro Apex One and Worry-Free Business Security Remote Code Execution Vulnerability

DESCRIPTION
Trend Micro has successfully addressed a zero-day vulnerability that could lead to remote code execution in the Trend Micro Apex One endpoint protection solution.
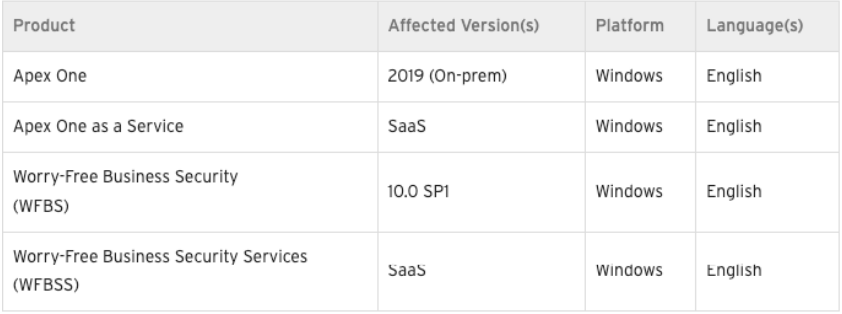
This vulnerability affects several Trend Micro products, including Trend Micro Apex One 2019, Trend Micro Apex One SaaS 2019, Worry-Free Business Security (WFBS) 10.0 SP1 (sold as Virus Buster Business Security (Biz) in Japan), and Worry-Free Business Security Services (WFBSS) 10.0 SP1 (sold as Virus Buster Business Security Services (VBBSS) in Japan).
TZero-Day Vulnerability: This is a vulnerability in software that has been discovered by an entity not previously affiliated with the software's producer. In this case, the zero-day vulnerability was found in the Trend Micro Apex One endpoint protection solution.
The vulnerability lies within a third-party software component included in the Trend Micro security product. In this case, the vulnerability exists in the uninstaller module from a third-party used within this software.
This vulnerability is rated high with a score of 9.1 based on the Common Vulnerability Scoring System (CVSS) version 3. This classification describes the vulnerability as "critical," indicating that it has serious potential for exploitation.
AFFECTED SYSTEMS
VULNERABILITY IMPACT
The impact of CVE-2023-41179, which is a zero-day vulnerability in Trend Micro's endpoint protection product, can be serious depending on how successfully attackers exploit it. In this context, here are some potential impacts that may occur if this vulnerability is exploited:
• Arbitrary Code Execution: CVE-2023-41179 is a remote code execution vulnerability. If exploited successfully, attackers can execute code with system-level privileges on the infected computer. This means they can take full control of the computer.
• Access to Administration Console: To exploit this vulnerability, attackers must have access to the administration console of the affected Trend Micro products. If successful, they can alter settings, disable protection, or even install malicious software on the infected computer.
• Potential Data Theft: In some cases, attackers who gain control of the system can use this access to steal sensitive data, such as financial information, customer information, or business secrets.
It is important to remember that the actual impact of this vulnerability will depend on how quickly mitigation measures are taken by the affected organization.
RECOMMENDATIONS
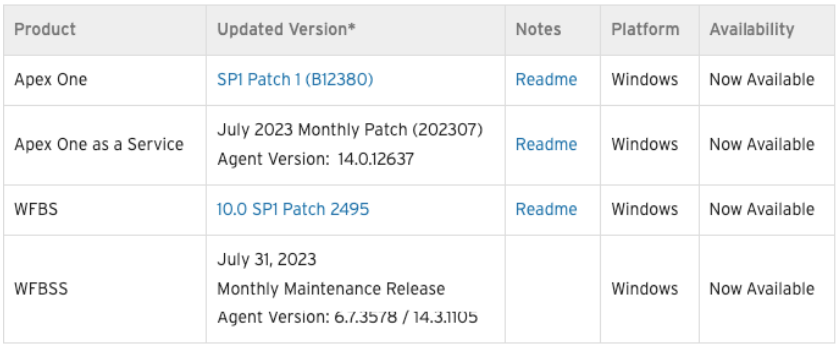
Trend Micro has released the following solution to address this issue: